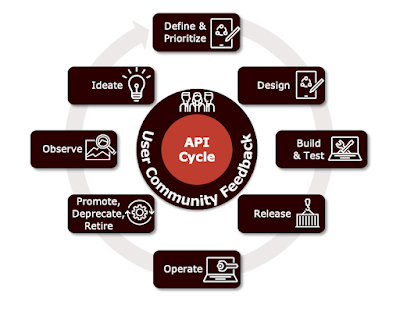
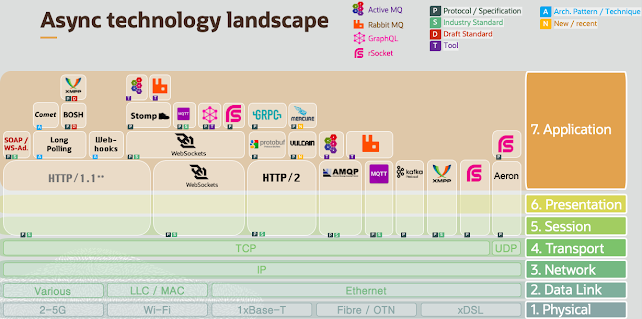
API Trends for 2024: A Glimpse into the Future of Interface Technologies

In 2023, the surge of Generative AI captured most of the spotlight in the tech world. I believe it marked an inflection point not just in how we interact with machines but also in society as a whole. As we move further into 2024, I believe that the API landscape is set to undergo a significant and profound evolution, I believe largely driven by the need to support a diverse array of new use cases emerging from what I like to call the AI Industrial Revolution. This post delves into the top trends in the API landscape, combining insights from my own experiences as an API product executive and practitioner, along with valuable perspectives by other API experts and thought leaders featured in the API Futures collection. Without further due, following my predictions for 2024: 1) The Rise of Polymorphic Interfaces for AI As Kristof van Tomme said on his article APIs are interface utilities : " As LLM AI systems start consuming APIs, this evolutionary block might get lifted. When AI-dri